In Might 2021, the President of the USA issued an govt order, beginning a government-wide effort to positive up its cybersecurity practices. The mandate tasked businesses with enforcing zero-trust architectures and a cloud-based infrastructure through 2024, aiming to extend safety and mitigate doable dangers.
However Carnegie Mellon College Electric and Pc Engineering Professor Virgil Gligor says the plan leaves a lot to be desired and explains attaining 0 believe is not conceivable.
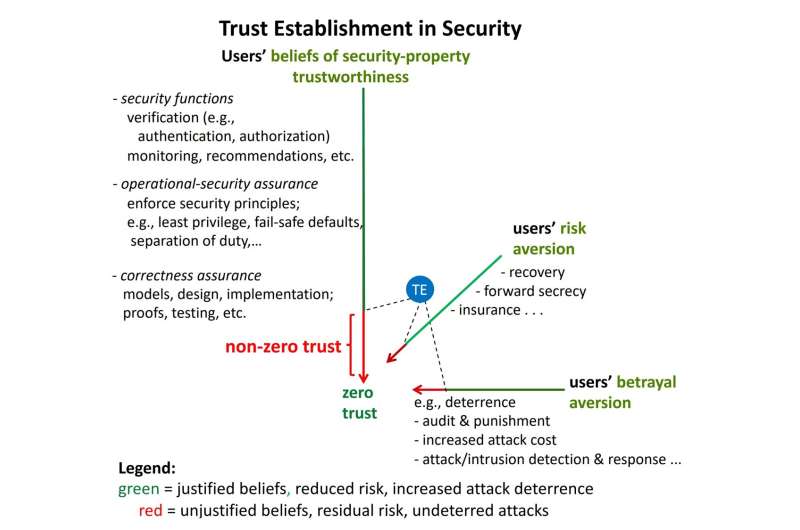
“Ahead of I inform you what 0 believe is, possibly I will have to get started through defining believe,” mentioned Gligor. “Believe is the acceptance of the reality of a observation with out proof or investigation; it’s blind religion or wishful considering if you’ll.”
“There are some spaces the place unjustified ideals are good enough, however in cybersecurity, believing {that a} safety assets holds with none proof or investigation is a legal responsibility. So, cybersecurity pros glance to get rid of blind ideals.”
To succeed in 0 believe, the absolute best stage of believe established order, Gligor says a number of tenets would need to be discovered. Most significantly, all safety homes of an undertaking community would need to be confirmed unconditionally and with simple task (i.e., with likelihood one in finite time).
“In case you are ready to do that, there is not any legal responsibility left; you will have reached 0 believe,” explains Gligor. “Sadly, that is theoretically not possible for some homes and almost unachievable for others.”
In his technical file, “0 Believe in 0 Believe?”, Gligor says that “black field” units, which might be utilized in all servers and endpoints of undertaking networks, make 0 believe unachievable, as there’s a minimum of one safety assets that can’t be justified unconditionally with simple task.
So, what does the federal government imply when it says 0 believe architectures? And what does it hope they are going to reach?
0-trust architectures don’t seem to be penetration resistant. Due to this fact, they don’t get rid of breaches. Gligor says, through enforcing those architectures, the federal government’s number one purpose is to restrict adversaries’ ‘lateral’ motion through segmenting networks so to scale back the quantity of wear an adversary could cause.
To safe those community segments or implicit believe zones, the federal government outlines a plan that might grant get right of entry to to sources according to steady verification of customers’ attributes (e.g., roles, permissions, get right of entry to ranges) and implement the least privilege theory (a safety idea that states a consumer or entity will have to simplest have get right of entry to to the particular knowledge sources and programs had to entire a required activity). On the other hand, Gligor says this idea is technically unsound.
Proscribing ‘lateral’ adversary motion can simplest be accomplished if the continual verification assessments and alertness of least privilege important save you move zone-attacks. Steady tracking of units’ behaviors will have to additionally come across them. However Gligor explains that zero-trust architectures continuously fail to come across and save you towards these kind of assaults, mentioning a number of examples in his technical file.
“The purpose of proscribing adversaries’ motion to a minimized believe zone can’t be completed for the reason that standards that 0 believe architectures use fail to attenuate many essential believe zones,” says Gligor.
“A number of different minimization rules exist, which 0 believe architectures forget about for sensible causes. Their implementation will require safety redesign, which the federal government seeks to keep away from as it might extend deployment.”
Whilst Gligor says 0 believe architectures can not function safety fashions because of their incapacity to counter main safety exposures, he stresses they don’t seem to be unnecessary.
“Even if the architectures have a low protection price, they provide helpful breach restoration price.”
The usage of knowledge from IBM, Gligor displays that segmenting networks into minimized believe zones can considerably scale back the quantity of knowledge misplaced in a breach, lowering the entire price of restoration efforts.
“Whilst you get well knowledge after a breach, you will have to decide what number of data data have been misplaced. With 0 believe architectures, as an alternative of shedding 20 million data to an adversary, you may lose only one,000 as a result of you will have restricted the choice of data the adversary has get right of entry to to. Therefore, there’s a lot much less to get well.”
Additional information:
File: www.cylab.cmu.edu/_files/pdfs/ … ts/CMUCyLab22002.pdf
Quotation:
0 believe in ‘0 believe’ (2023, March 6)
retrieved 21 March 2023
from https://techxplore.com/information/2023-03-zero-trust-in.html
This record is matter to copyright. Aside from any truthful dealing for the aim of personal learn about or analysis, no
phase could also be reproduced with out the written permission. The content material is equipped for info functions simplest.
Supply Via https://techxplore.com/information/2023-03-zero-trust-in.html




